In a recent proof of concept, we needed to configure FortiManager and the FortiGates to work through a web proxy. We configured FortiManager to act as the FortiGuard proxy (or FortiGuard Distribution Server (FDS) in Fortinet-speak), that way we only had to modify the web proxy to permit FortiManager to reach out to FortiGuard’s Distribution Network (FDN). Then all the FortiGates connect to FortiManager for updates, simplifying the design and limiting the need for Internet access of Fortinet devices. Hopefully it’ll help you in your designs as it took quite a bit of time to nail down the FortiGuard resources to whitelist in the proxy.
Background
As far as FortiGate to FortiManager connectivity, FortiGates use the following ports that will need to be allowed:
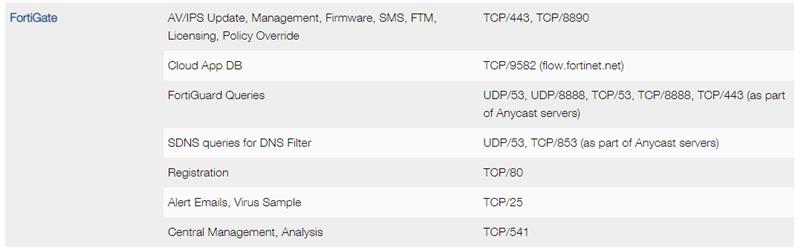
Specifically for us, we noticed traffic on TCP/443, TCP/8890 and TCP/8888 originating from the FortiGates destined for FortiManager (once we configured the FortiGates to use FortiManager for FortiGuard updates). Please double-check that that communication is allowed through your network.
Here is a list of observed domain names and IP addresses used for FortiGuard updates (as of 9/30/22):
service.fortiguard.net (AKA guard.fortinet.net)
173.243.138.194
208.184.237.61
209.222.147.36
usguard.fortinet.net
209.222.147.36
208.184.237.61 (same as service, guard)
update.fortiguard.net (AKA fds1.fortinet.com)
208.184.237.66
173.243.138.66
173.243.138.67
usfds1.fortinet.com
12.34.97.16
208.184.237.66
usfqsvr.fortinet.net
140.174.22.70
forticlient.fortinet.net
173.243.138.98
208.184.237.75
filestore.fortinet.com
154.52.23.130
productapi.fortinet.com
154.52.23.136
mapserver.fortinet.com
208.91.114.183
Domain Unknown (FortiGuard Package Updates, Entitlement)
66.117.56.42
66.117.56.38
12.34.97.72
12.34.97.71
We used that list to whitelist FortiManager communication to those IP addresses and domains without any MITM SSL inspection (for security reasons, FortiManager won’t trust any 3rd party certificates provided by the web proxy).
Option 1 – FortiGate uses Proxy
This option wasn’t ideal in our design because of the amount of work whitelisting in the web proxy, but I do want to at least touch on the topic of how to configure FortiGates to go through a web proxy. Here is the config for FortiGates to use a proxy:
config system autoupdate tunneling
set address <proxy_address>
set port <proxy_port>
set username <username>
set password <password>
set status {enable | disable}
end
However, consider the following:
- FortiOS connects to the proxy server using the HTTP CONNECT method. For information about the HTTP CONNECT method, see RFC 2616.
- FortiOS sends to the proxy server an HTTP CONNECT request that specifies the IP address and port required for the FDN connection. Authentication information is optional for the request.
- FortiOS must be configured to use DNS servers that resolve the addresses of FDN servers to support AV and IPS updates.
- The proxy server must not inspect the HTTPS traffic used for FortiOS communication.
- The proxy server establishes the connection to FDN and passes information between FortiOS and FDN.
- Proxy tunneling is supported only for registration, AV, and IPS updates. For FortiGate virtual machines, proxy tunneling can also be used for license validation. For web filtering or spam filtering, UDP protocol is used on ports 53 or 8888. UDP protocol traffic cannot be directed over a proxy server, even if you are using versions of FortiOS that support web filtering over port 443.
In a nutshell, it’s a pain.
Option 2 – FortiManager Uses Proxy
Another (perhaps better) option is for FortiManager to act as the FortiGuard proxy and you’ll point all the FortiGates to it. FortiManager systems acting as a local FortiGuard Distribution Server (FDS) synchronize their FortiGuard service update packages with the FortiGuard Distribution Network (FDN), then provide FortiGates these updates so that the FortiGates don’t need to reach out to the Internet themselves.
Step 1 – Whitelist the necessary connections in the Proxy
This is out of scope of this blog post, but in your proxy disable SSL inspection of FortiManager reaching out to the domain names/IP addresses above. FortiManager only supports simple authentication (username with password) and it’s only BASE64 encoded, so I’d also recommend disabling authentication between FortiManager and your proxy, if you require authentication.
Step 2 – FortiManager is configured to use the proxy
- Root ADOM > FortiGuard > AV & IPS Settings > Use Web Proxy > provide IP and port (optionally username/password)
- Root ADOM > FortiGuard > Web & Email Filter Settings > Use Web Proxy > provide IP and port (optionally username/password)
- Root ADOM > FortiGuard > Override FortiGuard Server (Local FortiManager) > enable AV & IPS Updates, enable Web & Email Filter Updates
- Click Apply
- If the FDN connection status is Disconnected, the FortiManager system is unable to connect through the web proxy.
Step 3 – FortiManager is configured to be FortiGuard Proxy
- Enable the FortiGuard Distribution Server (FDS) service on FortiManager’s network port
- Root ADOM > System Settings > Network > port1 > enable “FortiGate Updates” and “Web Filtering”, leaving bind to IP address as “0.0.0.0/0.0.0.0”.
- Connect the FortiManager system to the FortiGuard Distribution Network (FDN)
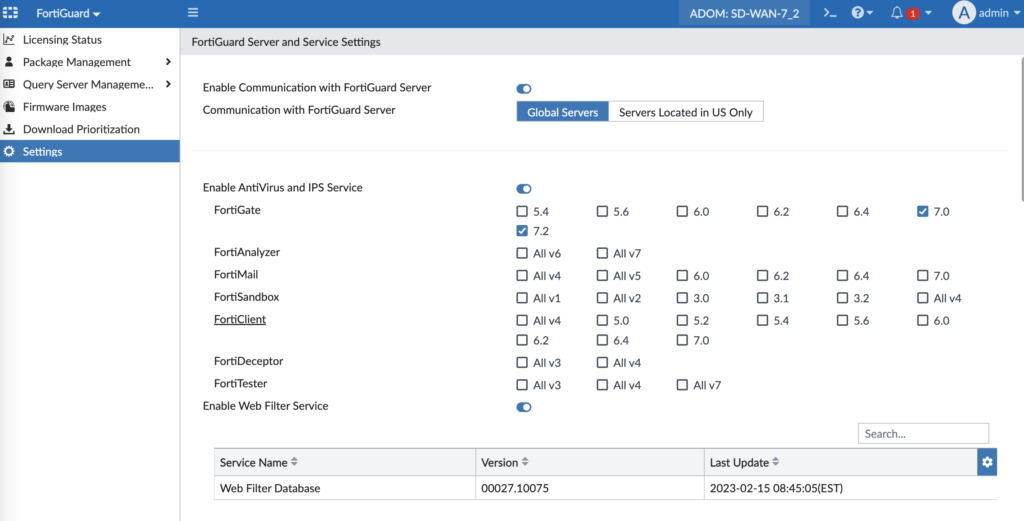
- Root ADOM > FortiGuard > Settings > Enable Communication with FortiGuard Server
- Root ADOM > FortiGuard > Settings > Enable AntiVirus and IPS Service
- Root ADOM > FortiGuard > Settings > Enable Web Filter Service
- Click Apply
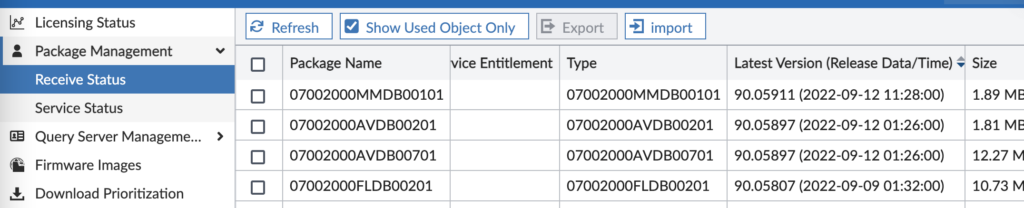
- Check if packages are being received under Root ADOM > FortiGuard > Package Management > Receive Status:
Step 4 – FortiGates are configured to use FortiManager as FortiGuard proxy
Point FortiGate to FortiManager for Updates:
config system central-management
set type fortimanager
set fmg “<FMG IP>”
set fmg-source-ip “<FGT IP>”
config server-list
edit 1
set server-type update rating
set server-address <FMG IP>
next
end
set include-default-servers disable
end
config system fortiguard
set fortiguard-anycast disable
set port 8888
set update-server-location usa
set source-ip <FGT MGMT IP>
end
Confirm FortiGate Receiving Updates:
- Compare a recently downloaded package on FortiManager with the version on FortiGate.
- Look at dates of FortiGate’s IPS, AV, etc. database updates and confirm they are recent.
- FortiGate > System > FortiGuard > Confirm green up arrows for web and anti-spam.
Option 3 – Manual Imports
Nobody likes Option 3, but it’s there if FortiManager is airgapped from the Internet. You download packages from a FortiManager instance with Internet access and then manually import them to the airgapped FortiManager. Here’s more information how to perform this method: https://docs.fortinet.com/document/fortimanager/6.2.7/new-features/561667/export-import-function-of-fortiguard-objects-for-fortimanager-in-a-closed-network
Troubleshooting
If FortiGuard is unreachable, follow these steps: https://community.fortinet.com/t5/FortiGate/Technical-Tip-FortiGuard-is-not-reachable-via-Anycast-default/ta-p/190041?externalId=FD50536
On FortiManager, confirm number of FortiGuard Lost Requests is 0:
diagnose debug rating
Locale : english
Service : Web-filter
Status : Enable
License : Contract
Service : Antispam
Status : Disable
Service : Virus Outbreak Prevention
Status : Disable
Num. of servers : 1
Protocol : https
Port : 8888
Anycast : Disable
Default servers : Not included
-=- Server List (Mon Sep 12 09:38:09 2022) -=-
IP Weight RTT Flags TZ FortiGuard-requests Curr Lost Total Lost Updated Time
192.168.5.105 -86 1 I M 0 43 0 0 Mon Sep 12 09:36:36 2022
To verify updates received by FortiGuard, verify FortiManager > FortiGuard > Package Management > Received Packages shows current database and date.
To verify updates received on FortiGate, compare a recently downloaded package on FortiManager with the version on FortiGate.
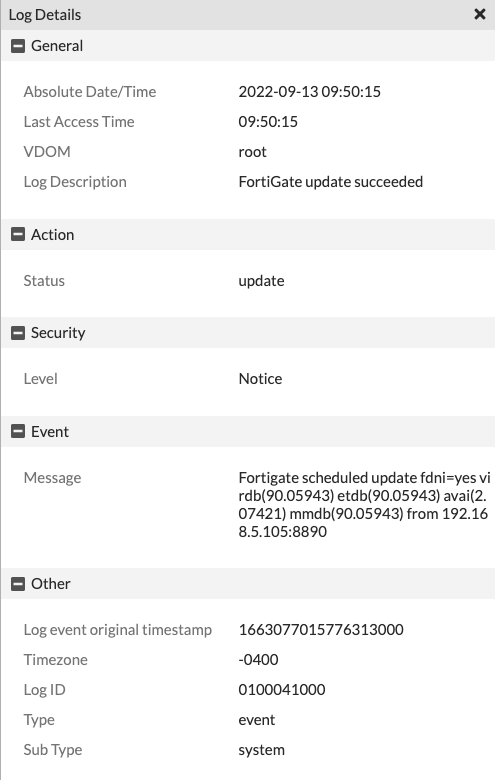
Check your FortiGate Logs for update events:
Conclusion
Hopefully that helps you in whichever situation you’re in. Option 2 is definitely the more scalable one and the option our customer chose. If you’ve run into this and would like to share any feedback, please leave a comment. And thanks for reading! Andrew