I have wanted to play with our FortiExtender for a while and finally got my hands on the FEX-511F! FortiExtender is more than just a cellular wireless WAN device to use as a cellular connection for a site, but can also be used for out-of-band management of the site if the primary WAN circuits go down. In this post I show how easy it is to setup and use FortiExtender.

Deployment Options
Standalone
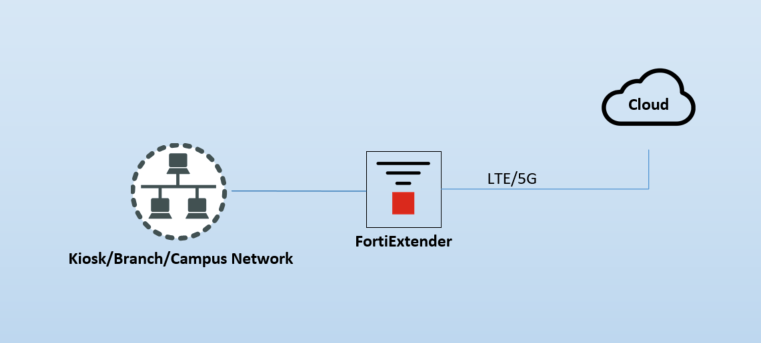
In Standalone mode, the FEX is independently managed (via HTTPS, SSH or console cable) and operates independently of a FortiGate firewall. It provides a site with cellular connectivity which is a perfect solution for a pop-up store, clinic or emergency operations center. While the FEX isn’t a NGFW with IPS functionality, it still operates as a Layer 4 firewall. It can perform NAT, simple SD-WAN steering and site-to-site VPN connectivity back to your data center.
FortiGate Managed
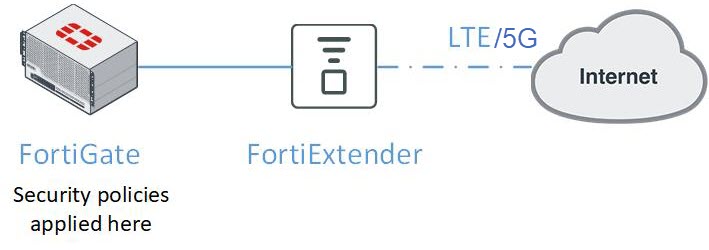
In FortiGate-Managed mode, the FEX acts as a pass-through device that converts CAT6 to cellular. The FEX itself is managed from the FortiGate and all of the routing, SD-WAN, NGFW, etc. is performed on the FortiGate.
FortiExtender Cloud Managed
This deployment mode is my favorite and you’ll soon see why. FortiExtender Cloud is a SaaS offering that allows web-based management of FEXs at scale. It is licensed per FortiExtender on a subscription basis. You can create configuration profiles, device groups, and mobile service plans across the entire globe. And the biggest feature I loved was the ability to use the FEX as an out-of-band management device to manage the FortiGate connected to it. FortiExtender Cloud is how I setup the FEX-511F in my lab and how I’ll walkthrough in this post.
FortiExtender Cloud Setup
FortiExtender Cloud is accessible from FortiCare or via https://fortiextender.forticloud.com/. Once you login to FortiExtender Cloud, you’ll see a nice dashboard of your deployed FortiExtenders:
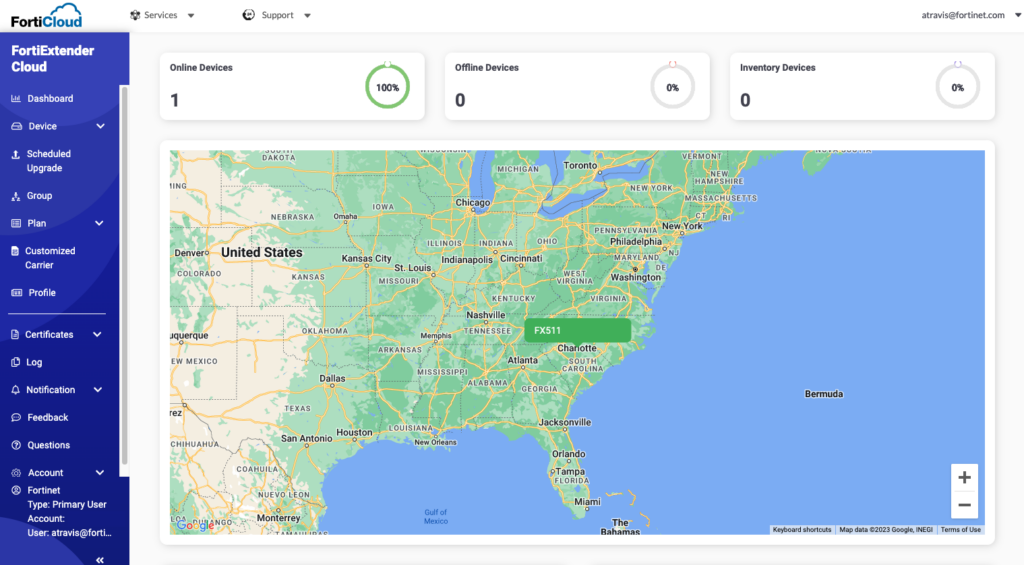
I just have one deployed here in Charlotte as shown on the dashboard. Under Plan, you’ll create one for each carrier and define any regional or modem attributes you’d like to define:
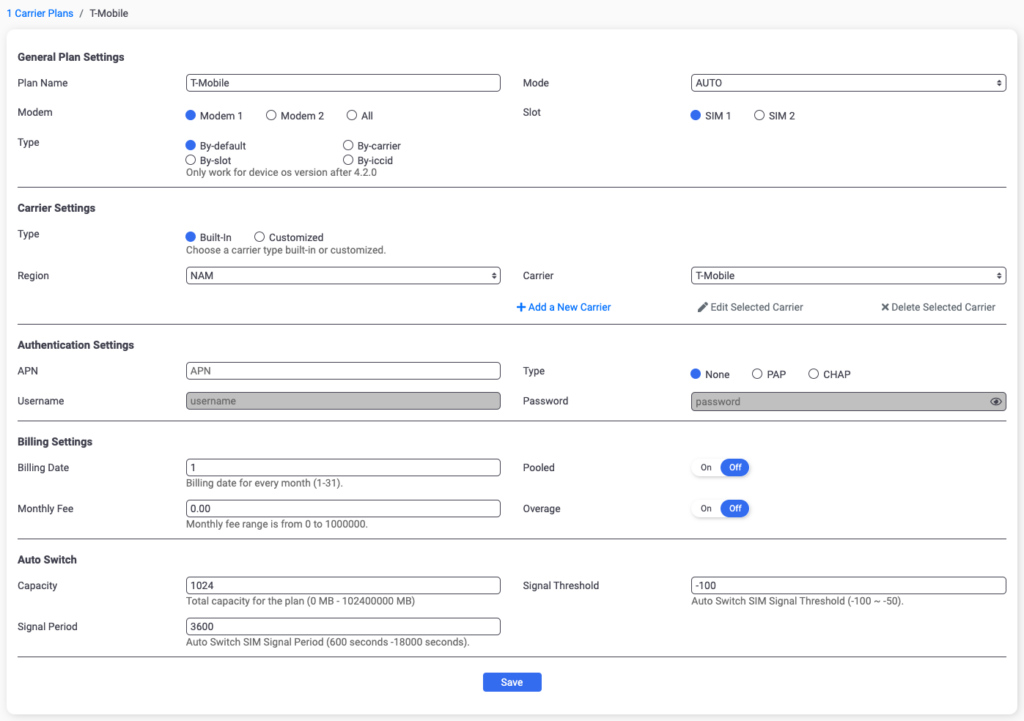
You can also configure these settings under FortiExtender Plans:
- Manage credential plans – create credential plans to configure device account credentials and apply them to profiles and individual devices.
- Manage network plans – define subnets, DHCP pools, etc. for the LAN interface(s) on the FEXs.
- Manage VPN plans – uses IPsec VPN to connect branch offices to each other; alternatively you can use FortiGates instead for more flexibility (i.e. ADVPN) while using the FEX for the cellular connectivity.
- Manage DNS Database plans – lets you create DNS Database plans to configure a FortiExtender as a DNS server.
FortiExtender Cloud allows you to create profiles tied to hardware and these profiles define admin access, passwords, firewall, routing, etc. Pretty much anything!
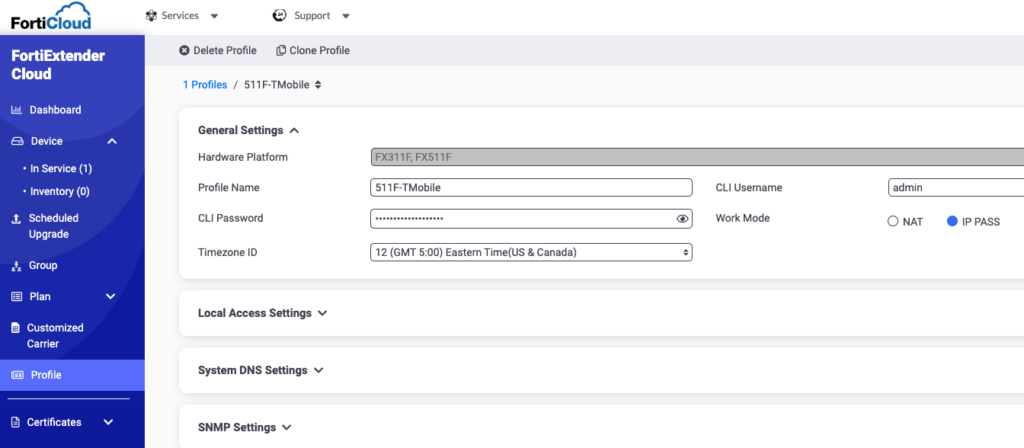
And lastly, you can create Groups to group your devices together that need to have similar plans, profiles, etc.
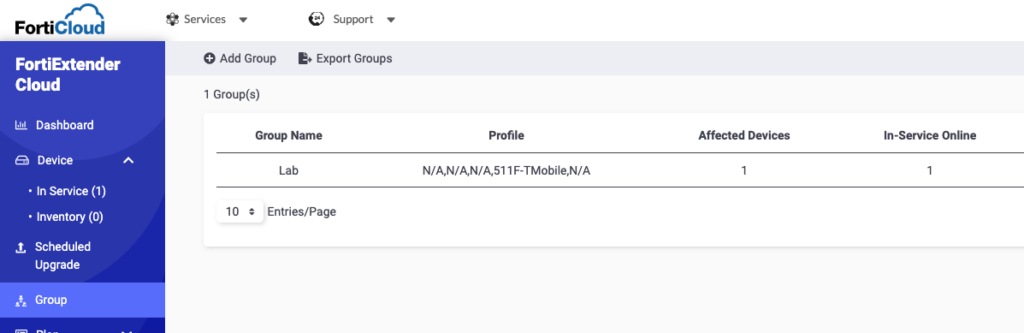
At this point, I see my FEX-511F under Device > Inventory and am able to assign my Profile and add it to my Group. After a few minutes, the status will change to online and the state to deployed:
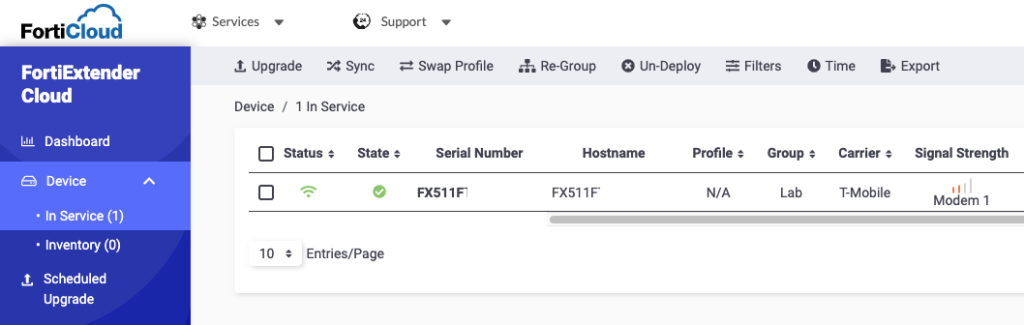
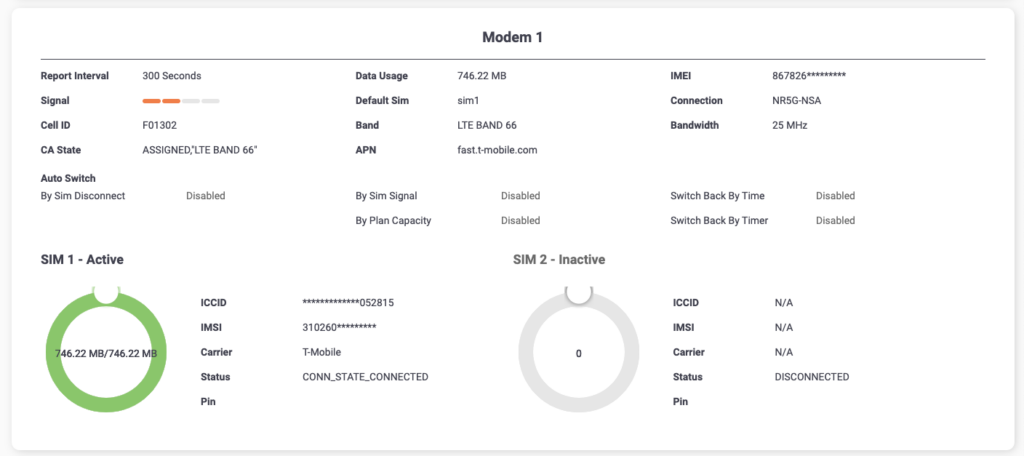
And when I drill into my FEX511F, I can see system information as well as cellular connectivity and throughput data:
FortiExtender Configuration
When the FortiExtender boots up, it cycles through the various modes of operation (standalone, FortiGate-managed and FortiExtender Cloud managed), so I didn’t have to configure anything on the FEX to tell it to use FortiExtender Cloud after I had deployed it in FortiExtender Cloud. But the following commands are useful to determine its status and ensure it’s managed by FortiExtender Cloud:
FX511 # get system status
Version: FXT511F-v7.4.1-build219 (GA)
Serial-Number: FX511Fxxxxxxxxxxxx
BIOS version: 00020001
System Part-Number: P26657-01
Burn in MAC: 94:f3:92:d0:34:c0
Model: FortiExtender-511F
Branch point: 219
Mode: CLOUD
Discovery-type: cloud
System time: Mon Oct 30 15:44:15 2023
FX511F # get extender status
Extender Status
name : FX511F
mode : CLOUD
fext-addr : 33.72.79.107
ingress-intf : lte1
fext-wan-addr : 33.72.79.107
controller-addr : fortiextender-dispatch.forticloud.com:443
deployed : true
account-id : 1228631
uptime : 2 days, 10 hours, 27 minutes, 46 seconds
management-state : CWWS_RUN
base-mac : 94:F3:92:D0:34:C0
network-mode : ip-passthrough
fgt-backup-mode : backup
discovery-type : cloud
discovery-interval : 5
echo-interval : 30
report-interval : 30
statistics-interval : 120
mdm-fw-server : fortiextender-firmware.forticloud.com
os-fw-server : fortiextender-firmware.forticloud.com
FortiGate View
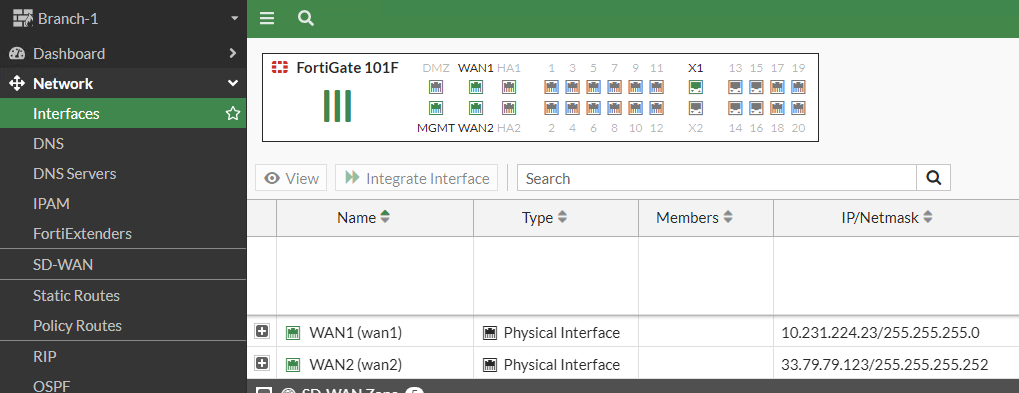
At this point, my FortiExtender is connected to cellular 5G/LTE and connected to one of the WAN ports on my lab’s FortiGate. Since we configured the FEX as “ip-passthrough” in the FortiExtender Cloud Profile assigned to the FEX, it is not performing any NAT or routing. And because it’s in passthrough, the FortiGate will see the public IP address provided by the active SIM on the FortiGate’s wan2 interface:
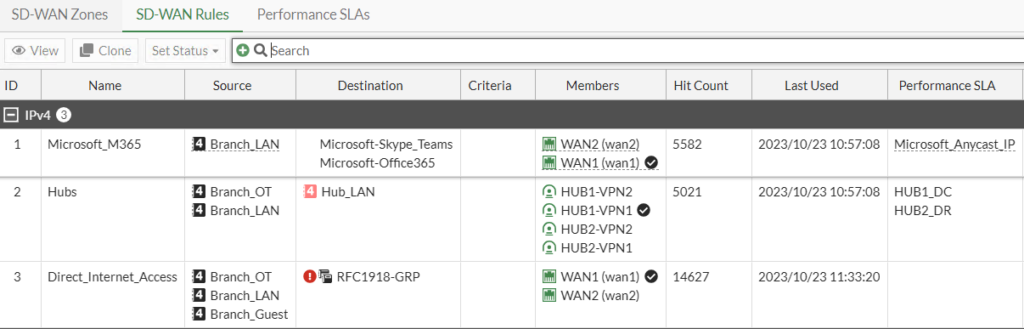
With the FEX connected to the FortiGate, I can use it for VPN connectivity as well as in my SD-WAN rules. Because the throughput on the 5G/LTE is lower and the latency higher than my primary Internet circuit, I configure it as the backup for my traffic:
Out of Band Management
Honestly the coolest factor for me with FortiExtenders is the out of band management functionality they provide. By simply connecting a Fortinet USB console cable to a device such as a FortiGate, I’m able to manage the FortiGate even if the primary wired Internet circuits go down and the FortiGate is unreachable. You can see in the picture below that I’ve connected the grey console cable to my FortiGate’s console port:

Now that the hard part (of plugging a cable) is complete, I’m able to access the FortiGate from FortiExtender Cloud by clicking the “OBM” button:
I confirm my serial port and baud rate:
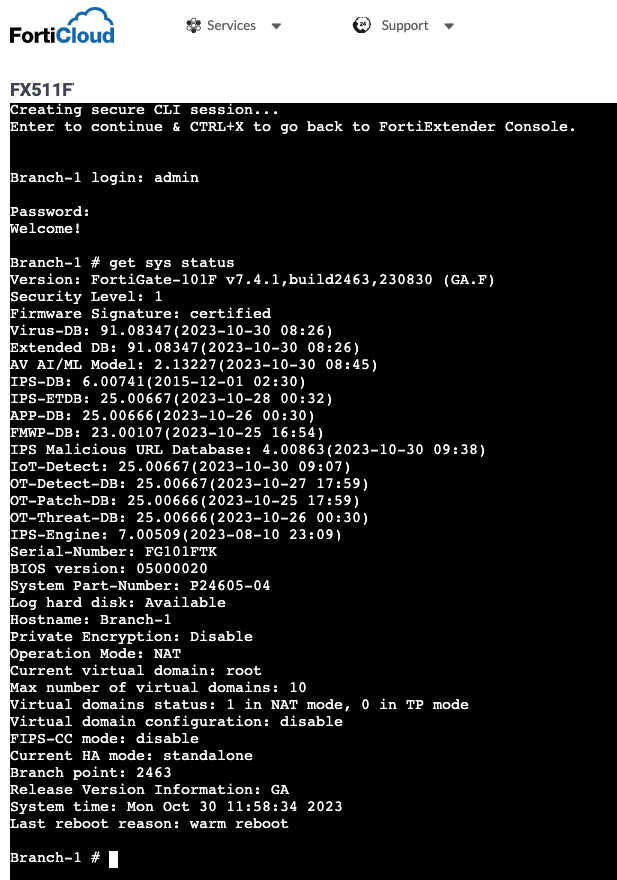
And now I’m able to login and enter any commands on the “Branch-1” FortiGate to troubleshoot and bring the site back online. How cool is that!
Conclusion
I’m barely scratching the surface on deployment models for the FortiExtender. Hopefully I’ll find time to test out the FortiGate-managed deployment next and use it with Zero Touch Provisioning. But until then, thanks for reading!

Great article. We have 2 Fortigates that run in HA connected with dark fiber (100m) apart on our campus.
With our 2 ISP handoffs we vlan them into a switch and then configure that vlan into both our gates so it doesn’t break the synchronization and each fortigate has a physical Ethernet going into it.
Most articles on Fortiextender seem to show the extender being close to the fortigate to plug it right in, but this wouldn’t work for us.
Curious if there is a way to basically make the Fortiextender act like a WAN handoff I could simply vlan?
Shannon, for this use-case I would probably setup the FEX in standalone mode on its own VLAN so that it’s not building a CAPWAP tunnel to either FortiGate and causing HA issues. Then the FEX will look like a WAN interface on both FortiGates via that VLAN sent down to the FortiGates. Please let me know if that works or you have more questions. Thanks! Andrew
Great article.
Wondering if you know of a way to to have the Fortiextender work in a such a way that it would be able to plug into both our Fortigates on our campus that connect with our dark fiber? Right now it’s in cap-wap mode and only is detected by one fortigate causing HA sync issues.
Normally with our 2 ISP circuits i land them in a switch and use a vlan to plug them into both our fortigates.
Would the Fortiextender need to be run in vlan-mode to sort of emulate an ISP circuit and vlan it the way same way I would an ISP circuit?