In a past blog post, I blogged about the various zero touch and low touch provisioning options when setting up new FortiGates. Since then, Fortinet has released FortiZTP to simplify zero touch provisioning further than what FortiDeploy provided. FortiDeploy used FortiGate Cloud to point FortiGates to FortiManager, but it only supported FortiGates and FortiAPs. The new FortiZTP offering simplifies the provisioning, making the process much more intuitive for FortiGates, FortiAPs, FortiSwitches and FortiExtenders. The table below highlights FortiZTP supported devices as well as which Fortinet device is compatible with which management platform (as of this post’s date):
It’s worth noting that in this blog post I only focus on FortiZTP for FortiManager (on-prem or Cloud) and not on FortiGate Cloud, FortiLAN Cloud, etc. because my customers utilize FortiManager for its features, so it’s where I spend more of my time.
Overview
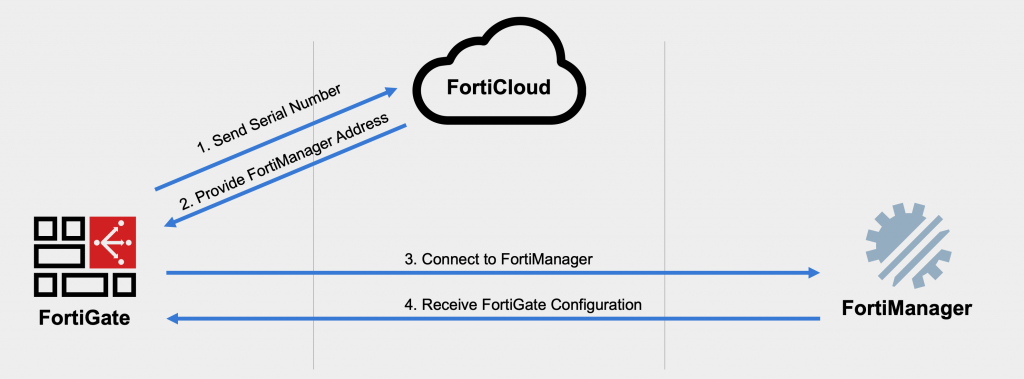
When a new (or factory reset) FortiGate boots up, it phones home to FortiCloud to see if FortiZTP has been configured. If you’ve configured FortiZTP to use FortiManager (or FortiGate Cloud, FortiLAN Cloud, FortiManager Cloud, FortiSASE, etc.), then FortiCloud will provide the FortiManager IP address and serial number to the FortiGate. The FortiGate will then connect to FortiManager and show up as either an unauthorized device or begin provisioning (if you’d preconfigured the FortiGate in FortiManager).
Configuration
For FortiZTP to work, you either need to make your FortiManager publicly accessible on port TCP/541 (link for all FortiManager ports for reference) or utilize FortiManager Cloud (our SaaS offering). You also need your ISP to provide your FortiGate a DHCP address (with default route) or FortiZTP won’t be an option because the FortiGate won’t automatically try and reach out; another option when DHCP isn’t available includes shipping the FortiGate to the destination with a USB drive containing just enough configuration to get it onto the Internet to use FortiZTP. I’m going to use an on-premise FortiManager that’s “publicly” accessible for my lab’s internal network.
Your first step is to register your devices in FortiCare for them to show up in FortiZTP; you can also work with your sales team to include a “bulk key” at time of order to auto-register the devices for you, which is handy if you have a lot of devices to register. FortiZTP is accessible at fortiztp.forticloud.com. Once you login with your FortiCare account, you’ll see a list of your registered devices:
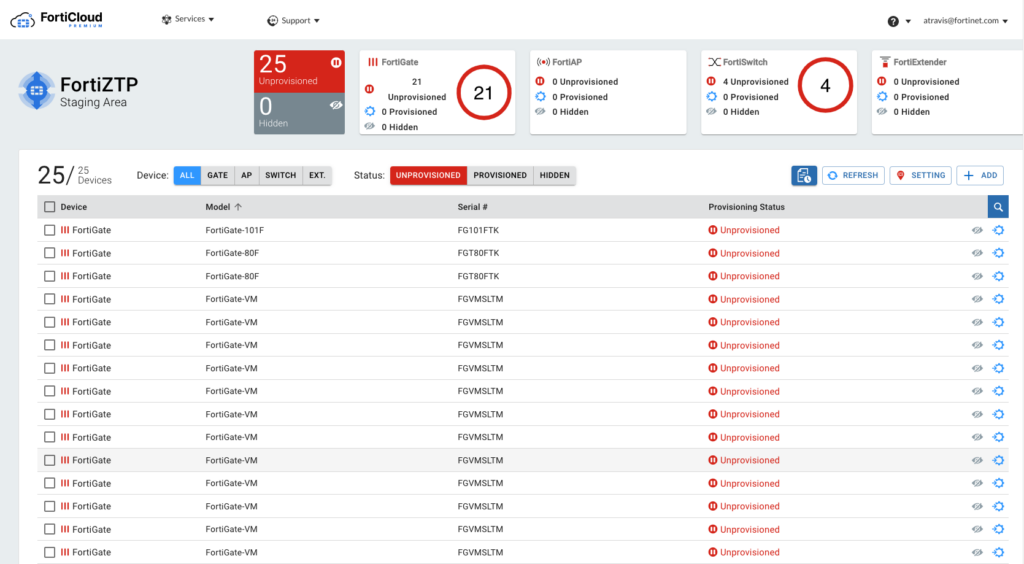
You’ll note that they are all Unprovisioned at the beginning. Our next step is to configure FortiZTP with our FortiManager settings. To do this, we’ll click on Settings on the top-right and enter the following information and click Update:
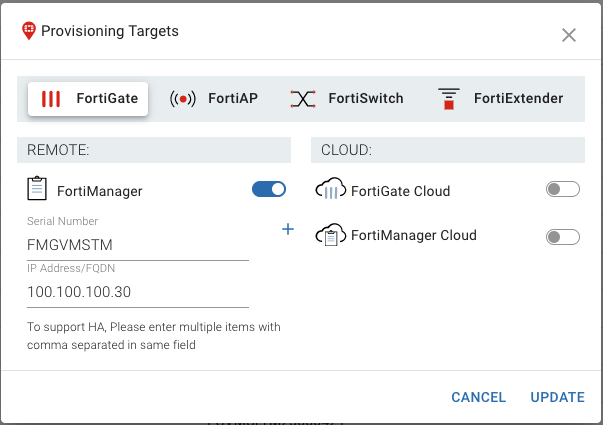
I selected the checkboxes of all my lab FortiGates and click Provision on the top-right of the screen.
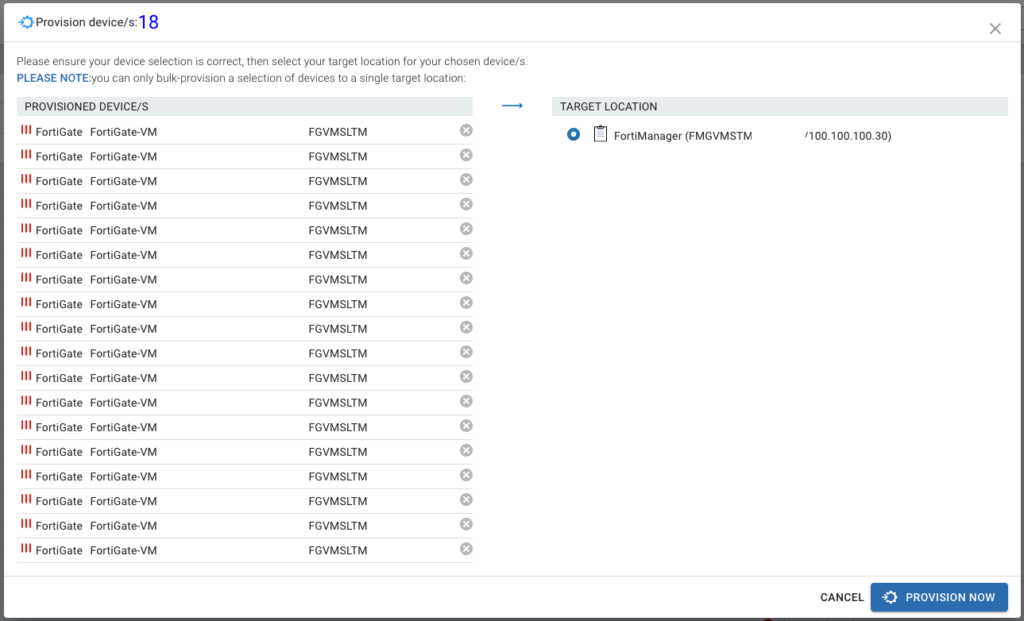
Now when we boot any of these FortiGates, they will try and reach our FortiManager at 100.100.100.30 (which is a “public” IP address in my internal lab for FortiManager).
Testing
To test this all out I factory reset my FortiGate 80F and deleted it from FortiManager. Once I booted the FortiGate 80F, I saw that FortiZTP successfully configured the central management portion:
FortiGate-80F # show system central-management
config system central-management
set type fortimanager
set fmg “100.100.100.30”
end
And just like magic, it showed up in my FortiManager as an unauthorized device awaiting authorization and configuraiton:
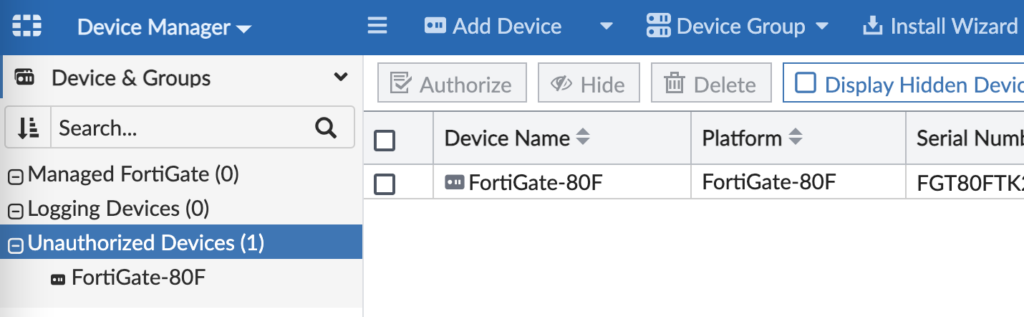
Now I can move the device to the appropriate FortiManager ADOM, assign my provisioning templates to it and push security policies to it.
Conclusion
FortiZTP is the next evolution in zero touch provisioning of FortiGates, FortiSwitches, FortiAPs and FortiExtenders. It simplifies an already simple method to get your brand new devices into one of our management platforms. All that without having to send a technician onsite to configure the device from scratch locally. And best of all, it’s free!

Awesome write-up! I’m curious about the process for a WAN connection with a static IP. Will the USB config have to include the full config of the device or can it just include the interface’s IP and default route with the ISP’s GW?
Wilhuff, you’ll want to start with a full default config from a FortiGate and then change what you’d like. Typically I’ll use the config from a factory-reset FortiGate of the same model and just change the necessary config to get it on the network (like static IPs and default routes). You can also use FortiManager to Add a Model Device with a fake serial number (i.e. FGT80FTK12345678 for a FortiGate 80F) and then download the Factory Default config to edit and use; once you’ve added the Model Device, double-click the device in FortiManager and scroll down to the pane for “Configuration and Installation”, click the “0” next to Total Revisions and you’ll see a drop-down to “Download Factory Default”. I hope this helps and please let me know if you have any follow up questions. Thanks! Andrew